Running Wireshark against android
I recently purchased some Libratone Zipp Mini speakers that were on offer and wanted a way to control these through Home Assistant.
Without any public API available I found an awesome post by Benjamin Hanke documenting his journey on reverse engineering the basic controls for controlling this device.
However I noticed there were some aspects missing such as getting the now playing information which would be useful for supporting this device as a Media Player.
After struggling with a variety of emulators that would not load the application due to missing libraries I looked into an alternative solution which lead me to a blog post by Martin Sauter involving installing tcpdump on your rooted Android device and redirecting the pcap dump to Wireshark on your laptop.
Setting up the Android device (rooted)
My device is running LinageOS 17.1 and is rooted allowing me to run applications that require root permissions such as tcpdump.
First you must enable developer options on your device.
Once enabled enable both “Android Debugging” and “Rooted debugging” from the developer options.
On the host
Now from your Linux computer you need to install Android Debug Bridge (adb) and Wireshark. Once installed you will now need to pair your phone:
sudo adb devices
Note: you must accept the debug request from your device
Next lets enable adb in root mode:
adb root
Finally lets shell into the device and check if tcpdump is installed.
adb shell
which tcpdump # should return something like /system/bin/tcpdump
For my custom firmware it looks like it came bundled with it. If this does not return a path to tcpdump then you will need to install this on your device. You have have luck following this guide.
If tcpdump is now found all that’s left is to run the following:
adb exec-out "tcpdump -i any -U -w - 2>/dev/null" | sudo wireshark -k -S -i -
This will run tcpdump on the device and return the stream back to the host piping this through to Wireshark.
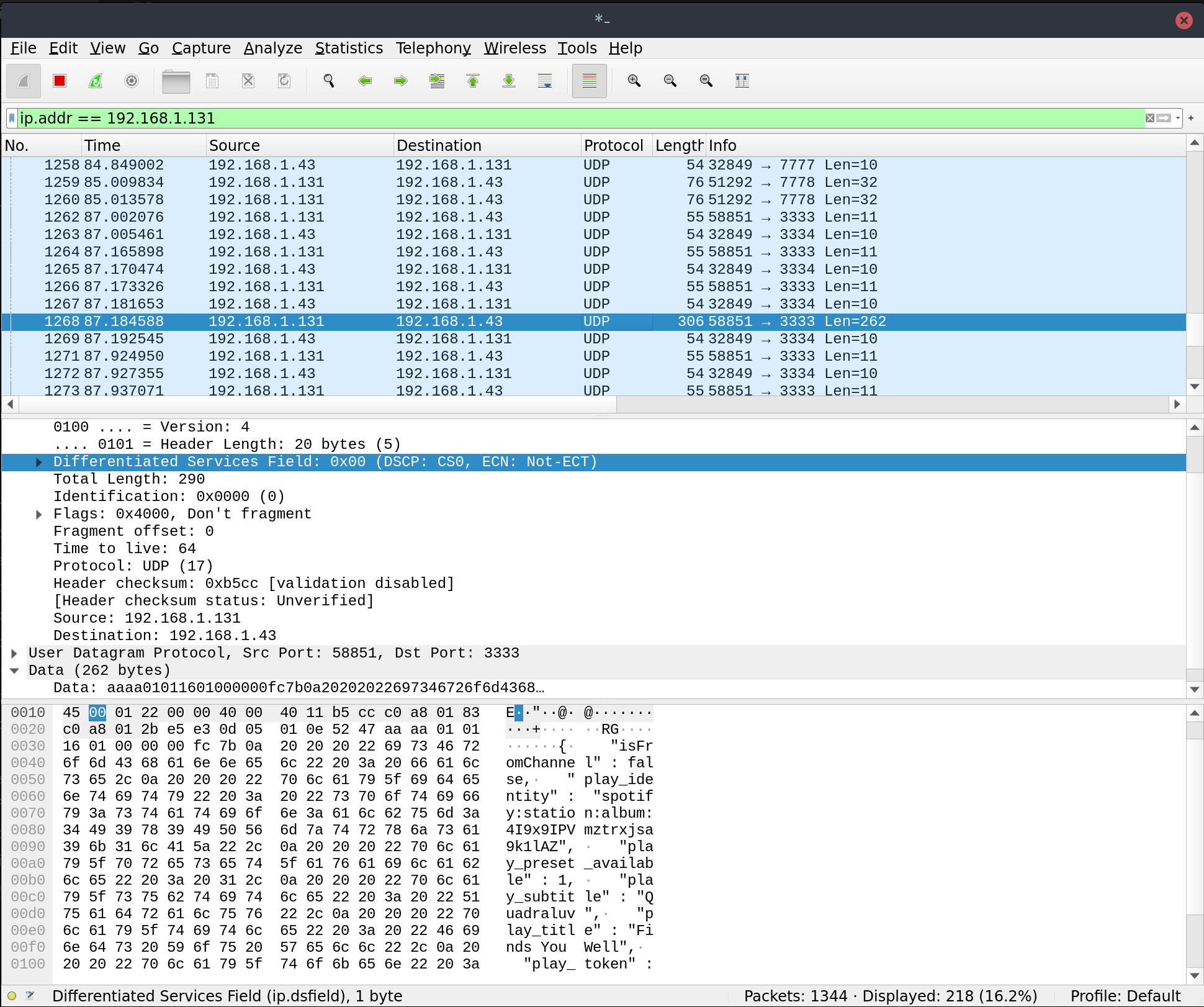
From here you can now inspect all the traffic happening on the device which can be quite noisy. To make it easier to find only the communication between your Android device and the Libratone you can Use an IP filter.
Which in my case is running on 192.168.1.131 and can be applied on the top bar like:
ip.addr == 192.168.1.131
That’s it for now. I will update with more once I have figured out what network calls are relevant!